Description
Introduction
Data Security in Hive as big data grows in scale and complexity, securing the data is more important than ever. Apache Hive, a data warehouse system built on top of Hadoop, is widely used for managing large datasets and running queries for data analysis. However, with the growing volume of sensitive information, ensuring that data within Hive is protected becomes a critical consideration for organizations.
This course focuses on implementing robust data security measures in Hive to control access, protect sensitive data, and ensure that queries and operations are executed securely. You will learn best practices for configuring authentication and authorization, encrypting data at rest and in transit, and auditing operations within Hive. By the end of this course, you will have the knowledge and skills to secure large datasets in Hive and comply with security regulations.
Prerequisites
- Basic understanding of Hadoop and the Hive architecture.
- Familiarity with relational databases and SQL.
- Understanding of data security principles and tools.
- Basic knowledge of Linux and system administration.
Table of Contents
- Introduction to Data Security in Hive
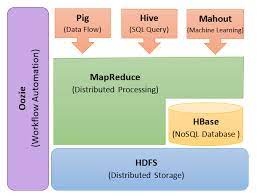
1.1 What is Hive and Why Security Matters?
1.2 Overview of Hive’s Data Architecture
1.3 Key Security Challenges in Big Data Systems
1.4 Understanding the Need for Security in Hive - Authentication and Authorization in Hive
2.1 Configuring Hive Authentication Mechanisms
2.2 Using Kerberos Authentication for Secure Access
2.3 Role-Based Access Control (RBAC) in Hive
2.4 Granting and Revoking Permissions in Hive
2.5 Integration with LDAP for Enterprise Authentication
2.6 Managing User and Group Access in Hive - Encrypting Data in Hive
3.1 Importance of Data Encryption in Big Data Systems
3.2 Encrypting Data at Rest in Hive(Ref: Mastering Progress: Building Scalable Applications with OpenEdge)
3.3 Enabling Transparent Data Encryption in Hive
3.4 Encrypting Data in Transit: Securing HiveQL Connections
3.5 Using SSL/TLS for Secure Hive Communication
3.6 Integration with Hadoop’s Encryption Framework - Audit Logging and Monitoring in Hive
4.1 Overview of Hive Auditing and Monitoring Features
4.2 Enabling Hive Audit Logging for Security and Compliance
4.3 Setting Up Hive Query Logging
4.4 Monitoring Data Access and Query Execution
4.5 Detecting and Responding to Security Incidents
4.6 Integrating with Apache Ranger for Centralized Auditing - Securing Hive Metastore
5.1 Understanding the Hive Metastore and its Security Risks
5.2 Protecting Metadata with Hive Metastore Security
5.3 Encrypting Hive Metastore Connections
5.4 Securing Hive Metastore with Kerberos
5.5 Backup and Recovery Strategies for Hive Metastore - Implementing Fine-Grained Access Control in Hive
6.1 What is Fine-Grained Access Control (FGAC)?
6.2 Using Apache Sentry for Fine-Grained Permissions
6.3 Managing Column and Row-Level Security in Hive
6.4 Creating Custom Security Policies in Hive
6.5 Integrating with Apache Ranger for Advanced Access Control - Data Masking and Redaction in Hive
7.1 What is Data Masking and Why is it Important?
7.2 Techniques for Implementing Data Masking in Hive
7.3 Redacting Sensitive Information in Queries
7.4 Use Cases for Data Masking in Big Data Analysis
7.5 Integration with Third-Party Data Masking Tools - Compliance and Regulatory Considerations
8.1 Data Security Regulations Affecting Hive (GDPR, CCPA, etc.)
8.2 Understanding Compliance Requirements for Big Data
8.3 Implementing Compliance Controls in Hive
8.4 Secure Data Sharing and Data Residency in Hive
8.5 Auditing Hive Data for Compliance with Regulatory Standards - Best Practices for Data Security in Hive
9.1 Security by Design: Building Secure Hive Systems
9.2 Keeping Hive and Hadoop Systems Updated and Patched
9.3 Using Encryption and Access Control Together
9.4 Reducing Attack Surfaces and Hardening Hive Configurations
9.5 Periodic Security Reviews and Vulnerability Assessments - Case Study: Implementing Data Security in Hive
10.1 Problem Definition and Security Goals
10.2 Configuring Authentication and Authorization
10.3 Implementing Encryption and Data Masking
10.4 Auditing and Monitoring for Compliance
10.5 Security Challenges and Mitigations in the Case Study - Conclusion
11.1 Recap of Key Data Security Concepts in Hive
11.2 Best Practices for Securing Data in Hive
11.3 Future Directions for Data Security in Big Data Ecosystems
11.4 Continuing Your Learning Journey in Big Data Security
Conclusion
By securing data in Hive, organizations can ensure that their large datasets are not only accessible but also protected from unauthorized access, loss, or breaches. Through effective authentication and authorization, data encryption, audit logging, and fine-grained access control, this course has provided the tools and techniques necessary for securing your data in Hive.
As the demand for big data grows, security will continue to play a crucial role in the success of any data-driven organization. By following the best practices outlined in this course, you can create a secure and compliant Hive environment capable of handling large-scale data while minimizing risks. Continue to explore emerging trends in data security and apply these concepts to enhance your data security strategy.







Reviews
There are no reviews yet.